From ZDNet ...
This time last year it was being reported that the Avalanche Gang was responsible for around a two thirds of all phishing attacks on the Internet. But Avalanche, described at the time as being "one of the most sophisticated and damaging on the Internet" by the Anti-Phishing Working Group (APWG) was only responsible for a paltry four conventional phishing attacks during the month of July 2010. Which you might think is good news, and it would be were it not for the fact that the Avalanche Gang has not hung up its spurs and given up cyber crime.
At the tail end of last year ZDNet UK reported that the Avalanche Gang, named after the botnet it employs, was collaborating with the people behind the Zeus botnet. Back then, in December 2009, Vincent Hanna who was employed as an investigator for the Spamhaus Project told ZDNet UK that the gangs behind Avalanche and Zeus were using each other's infrastructure on a purely commercial basis: "We see that the same viruses are emitting mails that benefit [the] different groups, either through spammed URLs or attached malware."
Fast forward to now, and it looks like the Avalanche Gang has completed its transition from conventional phishing and spam outfit to the world's biggest bank robbers. According to the latest APWG research, Avalanche has "moved from using conventional phishing to massively propagating stealthy password-stealing crimeware that does not require user cooperation to surrender financial account credentials."
The Avalanche Gang has been slowly ramping up a concerted campaign of crimeware propagation in order to con victims into getting infected by Zeus. Well, I say slowly, but everything is relative: according to the APWG research Avalanche has been sending billions of faked messages from tax authorities, false alerts/updates purporting to be from popular social networking sites, and other scams designed to deliver marks to drive-by download sites.
I have heard nothing to suggest that there is any evidence that Operation Trident Breach, an international effort involving the FBI and the Metropolitan Police as well as other law enforcement agencies around the world and which has so far led to the arrest of 150 people involved with the Zeus operation, has actually led to any arrests of Avalanche Gang members.
As Rod Rasmussen, co-author of the APWG research report, says: "Their spamming and other activities to target victims continues at high levels, implying they are finding malware distribution a more effective and profitable tactic than traditional phishing." With Zeus being responsible for hundreds of millions of pounds worth of theft to date, and no Avalanche arrests making the headlines, that would make the Avalanche Gang the most successful bank robbers in history.
Sunday, October 31, 2010
China Has Ability to Hijack U.S. Military Data, Report Says
From Jeff Bliss and Tony Capaccio at Bloomberg ...
China in the past year demonstrated it can direct Internet traffic, giving the nation the capability to exploit “hijacked” data from the U.S. military and other sources, according to a new report.
Recent actions raise questions that “China might seek intentionally to leverage these abilities to assert some level of control over the Internet,” according to excerpts from the final draft of an annual report by the U.S.-China Economic and Security Review Commission. “Any attempt to do this would likely be counter to the interests of the United States and other countries.”
On April 8, China Telecom Corp., the nation’s third-largest mobile-phone company, instructed U.S. and other foreign-based Internet servers to route traffic to Chinese servers, the report said. The 18-minute re-routing included traffic from the U.S. military, the Senate and the office of Defense Secretary Robert Gates.
“Although the commission has no way to determine what, if anything, Chinese telecommunications firms did to the hijacked data, incidents of this nature could have a number of serious implications,” the report said. The re-routing showed how data could be stolen and communications with websites could be disrupted, the report said.
Read more here ...
China in the past year demonstrated it can direct Internet traffic, giving the nation the capability to exploit “hijacked” data from the U.S. military and other sources, according to a new report.
Recent actions raise questions that “China might seek intentionally to leverage these abilities to assert some level of control over the Internet,” according to excerpts from the final draft of an annual report by the U.S.-China Economic and Security Review Commission. “Any attempt to do this would likely be counter to the interests of the United States and other countries.”
On April 8, China Telecom Corp., the nation’s third-largest mobile-phone company, instructed U.S. and other foreign-based Internet servers to route traffic to Chinese servers, the report said. The 18-minute re-routing included traffic from the U.S. military, the Senate and the office of Defense Secretary Robert Gates.
“Although the commission has no way to determine what, if anything, Chinese telecommunications firms did to the hijacked data, incidents of this nature could have a number of serious implications,” the report said. The re-routing showed how data could be stolen and communications with websites could be disrupted, the report said.
Read more here ...
iPwned!
From the MacRumors forum ...
When you iPhone is locked with a passcode tap Emergency Call, then enter a non-emergency number such as ###. Next tap the call button and immediately hit the lock button. It should open up the Phone app where you can see all your contacts, call any number, etc.Check out a video demo
My iPhone is jailbroken so that could be causing it. Can anyone confirm that it works on non-jailbroken iPhones?
Bug no iOS 4.1 from Salomão Filho on Vimeo.
stuxnet: targeting the iranian enrichment centrifuges in Natanz?
From Frank Rieger's blog ...
I did a writeup of the stuxnet story so far for the large german newspaper Frankfurter Allgemeine Zeitung (FAZ), out in print today (now also online here ). Unfortunatelly the page-one teaser image chosen by the frontpage editor is outright silly, and the picture chosen by the FAZ for the main piece is the reactor in Bushehr, as the facility in Natanz is optically less attractive. But, hey, the story is what counts. I want to comment on some of the more detailed aspects here, that were not fit for the more general audience of the FAZ, and also outline my reasoning, why I think stuxnet might have been targeted at the uranium centrifuges in Natanz, instead of Bushehr as guessed by others.
stuxnet is a so far not seen publicly class of nation-state weapons-grade attack software. It is using four different zero-day exploits, two stolen certificates to get proper insertion into the operating system and a really clever multi-stage propagation mechanism, starting with infected USB-sticks, ending with code insertion into Siemens S7 SPS industrial control systems. One of the Zero-Days is a USB-stick exploit named LNK that works seamlessly to infect the computer the stick is put into, regardless of the Windows operating system version – from the fossile Windows 2000 to the most modern and supposedly secure Windows 7.
The stuxnet software is exceptionally well written, it makes very very sure that nothing crashes, no outward signs of the infection can be seen and, above all, it makes pretty sure that its final payload, which manipulates parameters and code in the SPS computer is only executed if it is very certain to be on the right system. In other words: it is extremly targeted and constructed and build to be as side-effect free as humanly possible. Words used by reverse engineers working on the the thing are “After 10 years of reverse-engineering malware daily, I have never ever seen anything that comes even close to this”, and from another “This is what nation states build, if their only other option would be to go to war”.
Industrial control systems, also called SCADA, are very specific for each factory. They consist of many little nodes, measuring temperature, pressure, flow of fluids or gas, they control valves, motors, whatever is needed to keep the often dangerous industrial processes within their safety and effectiveness limits. So both the hardware module configuration and the software are custom made for each factory. For stuxnet they look like an fingerprint. Only if the right configuration is identified, it does more then just spreading itself. This tells us one crucial thing: the attacker knew very precisely the target configuration. He must have had insider support or otherwise access to the software and configuration of the targeted facility.
I will not dive very much into who may be the author of stuxnet. It is clear that it has been a team effort, that a very well trained and financed team with lots of experience was needed, and that the ressources needed to be alocated to buy or find the vulnerabilities and develop them into the kind of exceptional zero-days used in the exploit. This is a game for nation state-sized entities, only two handful of governments and maybe as many very large corporate entities could manage and sustain such an effort to the achievment level needed to build stuxnet. As to whom of the capable candidates if could be: this is a trip into the Wilderness of Mirrors. False hints are most likely placed all over the place, so it does not make much sense to put much time into this exercise for me.
Regarding the target, things are more interesting. There is currently a lot of speculation that the Iranian reactor at Bushehr may have been the target. I seriouly doubt that, as the reactor will for political reasons only go on-line when Russia wants it to go on-line, which they drag on for many years now, to the frustration of Iran. The political calculations behind this game are complex and involve many things like the situation in Iraq, the US withdrawal plans and Russias unwillingness to let the US actually have free military and political bandwith to cause them trouble in their near abroad.
But there is another theory that fits the available date much better: stuxnet may have been targeted at the centrifuges at the uranium enrichment plant in Natanz. The chain of published indications supporting the theory starts with stuxnet itself. According to people working on the stuxnet-analysis, it was meant to stop spreading in January 2009. Given the multi-stage nature of stuxnet, the attacker must have assumed that it has reached its target by then, ready to strike.
Read more here ...
I did a writeup of the stuxnet story so far for the large german newspaper Frankfurter Allgemeine Zeitung (FAZ), out in print today (now also online here ). Unfortunatelly the page-one teaser image chosen by the frontpage editor is outright silly, and the picture chosen by the FAZ for the main piece is the reactor in Bushehr, as the facility in Natanz is optically less attractive. But, hey, the story is what counts. I want to comment on some of the more detailed aspects here, that were not fit for the more general audience of the FAZ, and also outline my reasoning, why I think stuxnet might have been targeted at the uranium centrifuges in Natanz, instead of Bushehr as guessed by others.
stuxnet is a so far not seen publicly class of nation-state weapons-grade attack software. It is using four different zero-day exploits, two stolen certificates to get proper insertion into the operating system and a really clever multi-stage propagation mechanism, starting with infected USB-sticks, ending with code insertion into Siemens S7 SPS industrial control systems. One of the Zero-Days is a USB-stick exploit named LNK that works seamlessly to infect the computer the stick is put into, regardless of the Windows operating system version – from the fossile Windows 2000 to the most modern and supposedly secure Windows 7.
The stuxnet software is exceptionally well written, it makes very very sure that nothing crashes, no outward signs of the infection can be seen and, above all, it makes pretty sure that its final payload, which manipulates parameters and code in the SPS computer is only executed if it is very certain to be on the right system. In other words: it is extremly targeted and constructed and build to be as side-effect free as humanly possible. Words used by reverse engineers working on the the thing are “After 10 years of reverse-engineering malware daily, I have never ever seen anything that comes even close to this”, and from another “This is what nation states build, if their only other option would be to go to war”.
Industrial control systems, also called SCADA, are very specific for each factory. They consist of many little nodes, measuring temperature, pressure, flow of fluids or gas, they control valves, motors, whatever is needed to keep the often dangerous industrial processes within their safety and effectiveness limits. So both the hardware module configuration and the software are custom made for each factory. For stuxnet they look like an fingerprint. Only if the right configuration is identified, it does more then just spreading itself. This tells us one crucial thing: the attacker knew very precisely the target configuration. He must have had insider support or otherwise access to the software and configuration of the targeted facility.
I will not dive very much into who may be the author of stuxnet. It is clear that it has been a team effort, that a very well trained and financed team with lots of experience was needed, and that the ressources needed to be alocated to buy or find the vulnerabilities and develop them into the kind of exceptional zero-days used in the exploit. This is a game for nation state-sized entities, only two handful of governments and maybe as many very large corporate entities could manage and sustain such an effort to the achievment level needed to build stuxnet. As to whom of the capable candidates if could be: this is a trip into the Wilderness of Mirrors. False hints are most likely placed all over the place, so it does not make much sense to put much time into this exercise for me.
Regarding the target, things are more interesting. There is currently a lot of speculation that the Iranian reactor at Bushehr may have been the target. I seriouly doubt that, as the reactor will for political reasons only go on-line when Russia wants it to go on-line, which they drag on for many years now, to the frustration of Iran. The political calculations behind this game are complex and involve many things like the situation in Iraq, the US withdrawal plans and Russias unwillingness to let the US actually have free military and political bandwith to cause them trouble in their near abroad.
But there is another theory that fits the available date much better: stuxnet may have been targeted at the centrifuges at the uranium enrichment plant in Natanz. The chain of published indications supporting the theory starts with stuxnet itself. According to people working on the stuxnet-analysis, it was meant to stop spreading in January 2009. Given the multi-stage nature of stuxnet, the attacker must have assumed that it has reached its target by then, ready to strike.
Read more here ...
Indian OS
From Bruce Schneier ...
India is writing its own operating system so it doesn't have to rely on Western technology:
On the one hand, this is great. We could use more competition in the OS market -- as more and more applications move into the cloud and are only accessed via an Internet browser, OS compatible matters less and less -- and an OS that brands itself as "more secure" can only help. But this security by obscurity thinking just isn't true:
The only way to protect it is to design and implement it securely. Keeping control of your source code didn't magically make Windows secure, and it won't make this Indian OS secure.
India is writing its own operating system so it doesn't have to rely on Western technology:
India's Defence Research and Development Organisation (DRDO) wants to build an OS, primarily so India can own the source code and architecture. That will mean the country won't have to rely on Western operating systems that it thinks aren't up to the job of thwarting cyber attacks. The DRDO specifically wants to design and develop its own OS that is hack-proof to prevent sensitive data from being stolen.
On the one hand, this is great. We could use more competition in the OS market -- as more and more applications move into the cloud and are only accessed via an Internet browser, OS compatible matters less and less -- and an OS that brands itself as "more secure" can only help. But this security by obscurity thinking just isn't true:
"The only way to protect it is to have a home-grown system, the complete architecture ... source code is with you and then nobody knows what's that," he added.
The only way to protect it is to design and implement it securely. Keeping control of your source code didn't magically make Windows secure, and it won't make this Indian OS secure.
Labels:
Information Warfare,
policy,
privacy,
security,
Technology
The militarization of the Internet
Interesting thoughts on the militarization of the Internet from Susan Crawford ...
Someone needs to take a good hard look at those Internet surveillance stories being strategically placed on the front page of the New York Times.
There’s a trail here, I believe, that’s worth following. Here are some data points:
1. Cyberattack - there appears to be a deep interest in the ability to declare war online, as evidenced by cybersecurity research and public speeches by Herbert Lin, a key player who has worked on several cybersecurity reports for the National Research Council. Ethan Zuckerman has summarized a presentation by Lin, which included the following paraphrase of Lin’s remarks:
2. A “more authenticated Internet” would obviously include using the leverage provided by network operators to permit only fully-authorized, identified machines to connect. The ability to remotely disconnect machines or devices until they are cleansed is now within reach for federal networks - this same capability will inevitably spread to private connections.
3. A “more authenticated Internet” would also include more-easily tappable applications as well as machines. That’s what FBI Director Mueller is talking about in this video at 3:29.
4. There must be deep stress inside the USG re what the overall public position of the Administration will be on enhancing surveillance, authentication, and the ability to declare war online. Secretary Clinton’s “Internet Freedom” speech of January 2010 made clear that the free flow of information online is an important component of the nation’s foreign policy.
5. Given this stress, the agencies that are most interested in forwarding cyberattack abilities, surveillance, guaranteed back doors for encrypted communications, and all the other trappings of a “more authenticated Internet” have an interest in portraying their vision of the future Internet as inevitable. Part of that campaign would logically be to get the story into the mainstream media.
6. So, here we go - another front-page story yesterday in The Times: “Officials Push to Bolster Law on Wiretapping.” This is a hugely contentious issue. Should law enforcement be able to require all technologies online to have “back doors” allowing officials to (essentially) require that the same information be produced to them that was produced during the circuit-switched telephone era?
7. The Internet is not the same thing as a telephone network. It’s a decentralized agreement to route packets of information to particular addresses. It has made possible unparalleled innovation, free speech, and improvements to human lives around the world. Retrofitting it to make it fit law enforcement’s (or national security’s) “authentication” needs would be an enormous, retrograde step.
But it would certainly help us wage war online.
Someone needs to take a good hard look at those Internet surveillance stories being strategically placed on the front page of the New York Times.
There’s a trail here, I believe, that’s worth following. Here are some data points:
1. Cyberattack - there appears to be a deep interest in the ability to declare war online, as evidenced by cybersecurity research and public speeches by Herbert Lin, a key player who has worked on several cybersecurity reports for the National Research Council. Ethan Zuckerman has summarized a presentation by Lin, which included the following paraphrase of Lin’s remarks:
If we’re interested in pre-empting cyber attack, “you need to be in the other guy’s networks.” But that may mean breaking into the home computers of US citizens. To the extent that cloud computing crosses national borders, perhaps we’re attacking computers in multiple jurisdictions. Lin wonders whether a more authenticated internet will actually help us to pre-empt attack. And he reminds us that US Strategic Command asserts authorization to conduct “active threat neutralization” – i.e., logging into your machine to stop an attack in progress. . . .
Dr. Lin notes that it’s not a violation of international law to collect intelligence abroad. It’s possible to engage in covert action as regulated by US statute. And there’s an array of possible responses the US could launch in response to cyberattack (Lin pauses to note that he’s not advocating any of these) – we could attack enemy air defenses, hack their voting machines to influence an election, conduct campaigns of cyberexploitation to spy within those nations. Given all this, aren’t nations entitled to fear the consequences of a “free and open” internet? Might they reasonably choose to tighten national control over the internet?
2. A “more authenticated Internet” would obviously include using the leverage provided by network operators to permit only fully-authorized, identified machines to connect. The ability to remotely disconnect machines or devices until they are cleansed is now within reach for federal networks - this same capability will inevitably spread to private connections.
3. A “more authenticated Internet” would also include more-easily tappable applications as well as machines. That’s what FBI Director Mueller is talking about in this video at 3:29.
4. There must be deep stress inside the USG re what the overall public position of the Administration will be on enhancing surveillance, authentication, and the ability to declare war online. Secretary Clinton’s “Internet Freedom” speech of January 2010 made clear that the free flow of information online is an important component of the nation’s foreign policy.
5. Given this stress, the agencies that are most interested in forwarding cyberattack abilities, surveillance, guaranteed back doors for encrypted communications, and all the other trappings of a “more authenticated Internet” have an interest in portraying their vision of the future Internet as inevitable. Part of that campaign would logically be to get the story into the mainstream media.
6. So, here we go - another front-page story yesterday in The Times: “Officials Push to Bolster Law on Wiretapping.” This is a hugely contentious issue. Should law enforcement be able to require all technologies online to have “back doors” allowing officials to (essentially) require that the same information be produced to them that was produced during the circuit-switched telephone era?
7. The Internet is not the same thing as a telephone network. It’s a decentralized agreement to route packets of information to particular addresses. It has made possible unparalleled innovation, free speech, and improvements to human lives around the world. Retrofitting it to make it fit law enforcement’s (or national security’s) “authentication” needs would be an enormous, retrograde step.
But it would certainly help us wage war online.
Bredolab botnet shut down
From F-Secure ...
The Dutch National Crime Squad has announced a major takedown. The people behind the botnet have not been caught, but the servers (hosted in LeaseWeb IP space) have been taken over, effectively shutting down the botnet.
Bredolab is a large family of complicated, polymorphic trojans. They have been distributed via drive-by-downloads and email. Bredolab is known to be connected to email spam campaigns and rogue security products. And the size of the botnet was massive: over 30 million infected computers and close to 150 command & control servers.
Interestingly, the crime squad has announced that they will be sending a warning to infected PCs: "Users of computers with viruses from this network will receive a notice of at the time of next login with information on the degree of infection."
So they will probably use the existing botnet infrastructure to send a program to all infected machines, showing them a warning.
This is rarely done because running code on somebody else's computer might be seen as "unauthorized use", possibly making it illegal - although the intentions are obviously good.
Here's a video with more information (Severe warning! It is in Dutch).
Updated to add: The Dutch police is redirecting Bredolab-infected computers to this help page.
Updated to add: A 27-year old man has been arrested in Armenia. He is under investigation for being one of the operators behind Bredolab.
The Dutch National Crime Squad has announced a major takedown. The people behind the botnet have not been caught, but the servers (hosted in LeaseWeb IP space) have been taken over, effectively shutting down the botnet.
Bredolab is a large family of complicated, polymorphic trojans. They have been distributed via drive-by-downloads and email. Bredolab is known to be connected to email spam campaigns and rogue security products. And the size of the botnet was massive: over 30 million infected computers and close to 150 command & control servers.
Interestingly, the crime squad has announced that they will be sending a warning to infected PCs: "Users of computers with viruses from this network will receive a notice of at the time of next login with information on the degree of infection."
So they will probably use the existing botnet infrastructure to send a program to all infected machines, showing them a warning.
This is rarely done because running code on somebody else's computer might be seen as "unauthorized use", possibly making it illegal - although the intentions are obviously good.
Here's a video with more information (Severe warning! It is in Dutch).
Updated to add: The Dutch police is redirecting Bredolab-infected computers to this help page.
Updated to add: A 27-year old man has been arrested in Armenia. He is under investigation for being one of the operators behind Bredolab.
Thursday, October 28, 2010
When You Think You Surf Anonymously But You Don’t
From Roman Huessy at Abuse.ch ...
Roman continues,
And Roman hammers his point home,
Many companies, military- and governmental-networks have banned social networking sites like Facebook, Twitter, MySpace &Co from their networks. For instance in August 2009 the U.S. Marine corps just banned Social Networking Sites (SNS) from their classified network.
Roman continues,
Often there are (legal and comprehensible) reasons to ban SNS from coperate- an governmental networks. But the problem is that often the responsible persons and/or administrators who decided to ban SNS don’t know the consequences that such a ban can trigger. Let me ask you: Do you really think that users will accept a ban of their *most-favorite-websites*? Of course most of the user won’t, so they will start trying digging holes in your coperate firewall and webproxies/gateways. The point I would like to outline in this post are the consequences you will trigger when banning social networks as well as the risks/threats which result out of this.
As said before, most user won’t accept a ban of SNS (and please belive me: that’s fact ). The first thing they will do after your ban becomes active is googling about by-passing your security infrastructure. The first thing your users will come accross are PHP-based web proxy scripts. One of the most popular PHP-based proxy script is called Glype: It’s a tiny, powerful and fast web proxy which is based on PHP. You just have to download the ZIP file, upload the “upload” folder to a webspace and start using your brand new webproxy. But WOW – hey, you even don’t have to install your own web proxy, you just can use sites like proxy[dot]org and get a fresh list of 5’000+ working web proxies!
What sounds like honey being poured down their back to your users is purly pain for the administrators and security folks of companies and governmental organizations: Within a few minutes users will be able to bypass security gateways easily. But let’t talk about the security risks of such Anonymous web proxies.
*** The bad things you don’t know about such proxies ***
Unfortunately the other site of the coin looks much worse:
You don’t know who run these proxies
You don’t know if these proxies are secure and clean from any malware and drive-bys
You don’t know the intentions of the persons who runs these proxies (maybe they have mean ill?)
But you have must be aware of one fact: Those proxies aren’t anonymous! Web Proxy scripts like Glype&Co have a free configurable option wheter the administrator of the (glype-) proxy wants to log the requests which are passing his proxy or not. And you can be sure that the most Glype administrators will do.
Let’s take a deeper look at the origin IP addresses which are using such Glype proxies. A huge part of the Glype users are users from:
Educational networks like schools and univiersities (trying to break the blockade of Facebook&Co on Edu-Networks)
Home users from DSL- and dialup accounts (trying to bypass the internet censoreship of their ISPs/country)
Beside those (mostly) legitimate traffic (generaly I don’t support internet censorship in any country – so in my opinion this is some kind of legitimate traffic), there is a lot of noise coming from governmental and military networks around the world. I wont name any countries, but you can be sure that dozens of countries are affected. Some of the affected departments and ministries are listed below (I have translated the most of them from other languages, so don’t assume all of them belongs to the US – they don’t):
Ministry of Foreign Affairs
Ministry of Finance
Ministry of Economy
Ministry of Statistics
Ministry of Administration and Interior
Ministry of Industry
Ministry of Interior and Justice
Ministry of Labour and Social Policy
Ministry of Social Development
Department of Defense
Department of Atomic Energy
Department of Health
Department of Science and Technology
Department of Home Affairs
Department of Water Affairs and Forestry
Department of Environment and Conservation
National Labratory
National Police Service
Residence of the President
Atomic Energy Comission
Centre for Atomic Research
State police
National Telecommunications Commission
Supervision and Administration Commission
State-owned news agency
Various Military Test- and Command Centres around the globe
Various networks which are just named as “Government of xxxx”
And Roman hammers his point home,
As I already pointed out I don’t see a problem in users bypassing internet censorship per se. They just have to know that they don’t really surf anonymously when they use such script based proxies (like Glype) and that those logfiles are propably accessible by anyone from anywhere.
But such proxies are becoming a problem as soon as they are used by employees of governmental and military organistaions (like shown above): These proxies could be a great resource for terroristic organization and foreign intelligence services! Many of the governmental traces I’ve seen are on facebook – so I was able to catch the names of employees of various governmental and military organizations. To show you the threat of such ‘information’ I will make real example which I saw in those logfiles.
You might have noticed that I mentioned Ministry of Foreign Affairs before (of a country which I won’t name here). While checking the logs I just came across a user who surfed on Facebook. The Logfiles provides a link to a profile of a employee of the Ministry of Foreign Affairs. When I checked the profile, I just noticed that this user is obviously a employee of the Security Service at the Ministry of Foreign Affairs. In fact, this person is now a high value target for terroristic organization and foreign intelligence services who are now able to get personal information about this person easily. This allows them to apply pressure and blackmail the person in order to gain access to classified information and documents.
*** Conclusion ***
My research on these Glype proxies allow me to make the following conclusions:
- Glype- (and other script based proxies) aren’t really anonymous
- You don’t know who runs these proxies
- Most users for those proxies just want to bypass internet censoreship of their country or schools/universities
- But there are many users from governmental and military organizations using those proxies too
- In those cases you may be able to hide your web traffic from your administrator but you will leave traces in other places which are probably a threat of your whole company!
- Administrators and security folks have to know about these risks and have to adopt compensating measures and/or providing awareness to its users
- If you run such a Glype proxy you have to know that you will propably be responsible for any illegal activites which are passing your proxy. Are you sure that your Glype proxy is not being abuse to access ilegal content like Childporn?
Transatlantic Views of Privacy
From Cecilia Kang at the Washington Post ...
This piece provides an interesting insight into how EU regulators approach privacy regulations - an approach that contrasts with how US regulators view privacy.
The federal government has ended an inquiry into a privacy breach involving Google's Street View service, satisfied with the company's pledge to stop gathering e-mail, passwords and other information from residential WiFi networks as it rolls through neighborhoods.
Wednesday's decision by the Federal Trade Commission is a sharp contrast with the reaction of regulators in Europe. The United Kingdom has launched a new investigation into Google's collection of unencrypted WiFi data, exposing the company to potential fines. Germany told Google to mark its Street View cars that take pictures of neighborhoods and homes. The Czech Republic banned Google from expanding its mapping software program.
The differences highlight an increasing gap between regulators in the United States, where the freewheeling Internet culture has birthed many of the social networking sites and search engines used worldwide, and governments in Europe and Canada, which tend to be much more aggressive about privacy.
"Part of it is cultural, and part of it is that the U.S. and Europe have radically different privacy regimes," said Chris Calabrese, legislative counsel for the ACLU. "The European model is extensive data protection in private information, and the U.S. model is piecemeal."
This piece provides an interesting insight into how EU regulators approach privacy regulations - an approach that contrasts with how US regulators view privacy.
Wednesday, October 27, 2010
Good news, of a kind, from a dark world
From Josephn Menn at BoingBoing ...
For those interested I strongly recommend you read Menn's book Fatal System Error.
As a fan of BoingBoing dating from a decade ago, when it was delivered on horseback, I wanted to share something positive with fellow readers in my first guest post. Unfortunately, the thing I've been most passionate about in my reporting and writing since 1999--cybercrime and tech security--doesn't lend itself to much that's happy. What I'm offering today is a compromise. It was good news to me personally, and it will be good news to those of you who have my read my book, Fatal System Error. For the rest of you, it won't be pleasant, and I'm sorry about that.
On Friday, I got a Skype message from a longtime source of mine: "My friend got his daughter back." We spoke on Sunday, and I will tell you what I can from that talk. To begin with, though, my source uses the fake name Jart Armin of HostExploit.
Like the people who work at Spamhaus, Jart is one of those people dedicated to tracking the worst cyber gangs who works in anonymity in order to protect himself. I don't like quoting people I can't name, but I did so in the book with Jart because he has done important research and because he is entirely right to be afraid of the people he has been tracking.
To explain that in the book, I briefly told the story of a colleague of Jart's who was investigating mob activity in St. Petersburg, Russia. The colleague made the mistake of working with the local police. Before he finished his assignment, the man's teenage daughter was kidnapped from her Western country, and the investigator got a message that if he dropped the case, the rest of his children might be okay.
That was five years ago. I had to leave the story hanging in the book because there had been no closure. A couple of weeks ago, the man got a new message. His daughter was in Kazakhstan, and he could have her back as long as he agreed not to look into certain of the gang's activities. One factor in the change of heart was the additional attention that Fatal System Error brought to the mob. The family has been reunited, though the young woman is not the same as she was. She was fed drugs and used to service men. A grim story, but at least it has an ending now, and I wanted to update those who knew the first part.
There are many reasons why cybercrime is as bad as it is, and getting much worse. One of them is lack of awareness of how dangerous and well-connected the gangs are. The most serious identity thieves and fraudsters are not isolated teenage script kiddies. They are mobsters who kill people, and worse, though those stories are seldom told. Folks need to know just how bad they are, every bit as much as they need to know the stories of the heroes who are risking their lives to stop them.
For those interested I strongly recommend you read Menn's book Fatal System Error.
Tuesday, October 26, 2010
Firesheep: who is eating my cookies?
We talked a bit about FireSheep yesterday in class. PandaLabs provides a good write-up on it here ...
Don’t panic. Yes, this is bad, but there are some countermeasures to take. The best solution would be to use SSL encryption in all communications, but this has to be supported in the server side, so that won’t be happening (at least massively) anytime soon. Meanwhile, you should use HTTPS Everywhere, which will force to use https when connecting to some mayor websites, such as Twitter or Facebook:

You can get HTTPS-EVERYWHERE from the EFF. They are a very, very reputable organization and I strongly recommend that you install this plug-in.
NOTE: This plug-in may still be vulnerable to Moxie Marlinspike's SSL-Strip attack but I have yet to verify that.
Special thanks to your classmate Sean for pointing out HTTPS-Everywhere. Good work Sean!
Monday, October 25, 2010
"Deleted" Facebook photos still not deleted: a followup
Via Jacqui Cheng at Ars Technica
Read more here.
Facebook may be making strides in some areas of privacy, but the company is still struggling when it comes to deleting user photos—or not deleting them, as the case may be.
We wrote a piece more than a year ago examining whether photos really disappear from social network servers when you delete them, and found that Facebook was one of the worst offenders when it came to leaving "deleted" photos online. We decided to revisit the issue recently when readers continued to point out that our deleted photos from that article were still online more than 16 months later. Indeed, this old photo of me remains on Facebook's content delivery network (CDN) servers, despite being deleted on May 21, 2009.
Read more here.
Sunday, October 24, 2010
Independent Myanmar Publication Claims Cyberattack
From the New York Times ...
BANGKOK — The Web site of The Irrawaddy, a magazine based in Thailand that is a leading source of news and criticism of the junta in Myanmar, has come under attack and been blocked by hackers, its editor, Aung Zaw, said on Monday.
The “distributed denial of service” attack just after midnight was similar but more sophisticated than an attack that forced the temporary closing of the site two years ago. Mr. Aung Zaw said it was not clear whether the attack came from inside Myanmar or from China, a close ally. Visitors to the Web site, www.irrawaddy.org, have been redirected to a mirror site while technicians seek to restore it.
“This is a new game, a new frontier” in the government’s struggle against its opponents, Mr. Aung Zaw said. “It shows how vulnerable we are.”
BANGKOK — The Web site of The Irrawaddy, a magazine based in Thailand that is a leading source of news and criticism of the junta in Myanmar, has come under attack and been blocked by hackers, its editor, Aung Zaw, said on Monday.
The “distributed denial of service” attack just after midnight was similar but more sophisticated than an attack that forced the temporary closing of the site two years ago. Mr. Aung Zaw said it was not clear whether the attack came from inside Myanmar or from China, a close ally. Visitors to the Web site, www.irrawaddy.org, have been redirected to a mirror site while technicians seek to restore it.
“This is a new game, a new frontier” in the government’s struggle against its opponents, Mr. Aung Zaw said. “It shows how vulnerable we are.”
M&A in the Underground Economy
From Krebs on Security ...
The rest of this post does an excellent job of describing the competitive dynamics in the underground marketplace. Read more here.
Leading malware developers within the cyber crime community have conspired to terminate development of the infamous ZeuS banking Trojan and to merge its code base with that of the up-and-coming SpyEye Trojan, new evidence suggests. The move appears to be aimed at building a superior e-banking threat whose sale is restricted to a more exclusive and well-heeled breed of cyber crook.
Underground forums are abuzz with rumors that the ZeuS author — a Russian hacker variously known by the monikers “Slavik” and “Monstr” — is no longer planning to maintain the original commercial crimeware kit.
According to numerous hacker forums, the source code for ZeuS recently was transferred to the developer of the SpyEye Trojan, a rival malware maker who drew attention to himself by dubbing his creation the “ZeuS Killer.” The upstart banking Trojan author constantly claimed that his bot creation kit bested ZeuS in functionality and form (SpyEye made headlines this year when investigators discovered it automatically searched for and removed ZeuS from infected PCs before installing itself).
The rest of this post does an excellent job of describing the competitive dynamics in the underground marketplace. Read more here.
Monday, October 4, 2010
Ukraine Detains 5 Individuals Tied to $70 Million in U.S. eBanking Heists
From Krebs on Security,
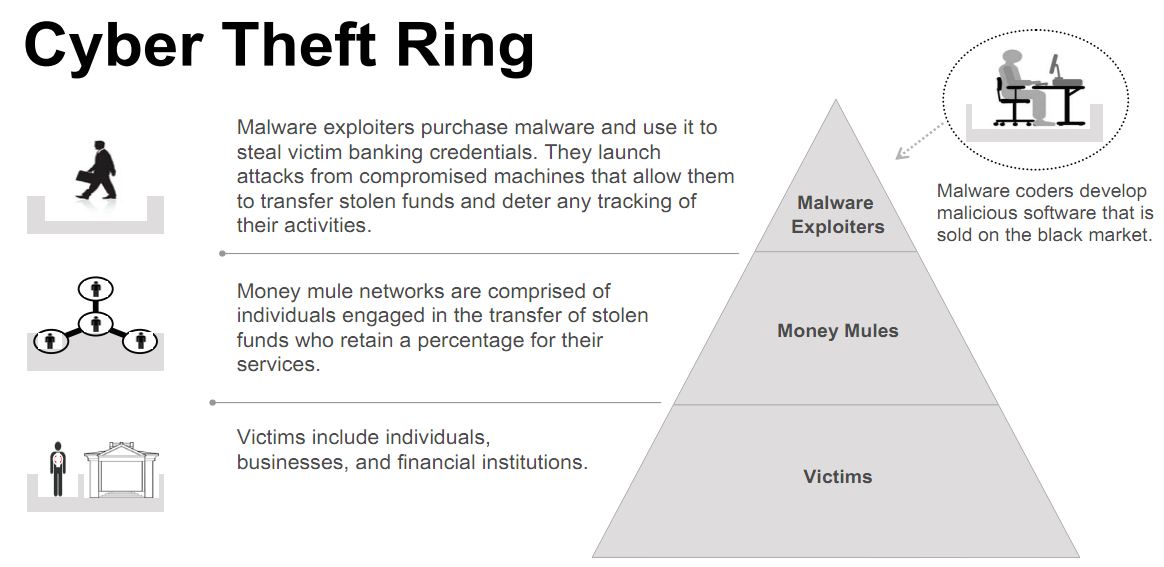
Authorities in Ukraine this week detained five individuals believed to be the masterminds behind sophisticated cyber thefts that siphoned $70 million – out of an attempted $220 million — from hundreds of U.S.-based small to mid-sized businesses over the last 18 months, the FBI said Friday..
At a press briefing on “Operation Trident Breach,” FBI officials described the Ukrainian suspects as the “coders and exploiters” behind a series of online banking heists that have led to an increasing number of disputes and lawsuits between U.S. banks and the victim businesses that are usually left holding the bag.
The FBI said five individuals detained by the Security Service of Ukraine (SBU) on Sept. 30 were members of a gang responsible for creating specialized versions of the password-stealing ZeuS banking Trojan and deploying the malware in e-mails targeted at small to mid-sized businesses.
Investigators say the Ukrainian gang used the software to break into computers belonging to at least 390 U.S. companies, transferring victim funds to more than 3,500 so-called “money mules,” individuals in the United States willingly or unwittingly recruited to receive the cash and forward it overseas to the attackers. In connection with the investigation, some 50 SBU officials also executed eight search warrants in the eastern region of Ukraine this week

New Clues Point to Israel as Author of Blockbuster Worm, Or Not
From Wired's Threat Level Blog,

Read more here
New clues released this week show a possible link between Israel and sophisticated malware targeting industrial control systems in critical infrastructure systems, such as nuclear plants and oil pipelines.
Late Thursday, security firm Symantec released a detailed paper with analysis of the headline-making code (.pdf), which reveals two clues in the Stuxnet malware that adds to speculation that Israel may have authored the code to target Iran.
Or, they could simply be red herrings planted in the code by programmers to point suspicion at Israel and away from other possible suspects.
The malware, called Stuxnet, appears to be the first to effectively attack critical infrastructure and in a manner that produces physical results, although there’s no proof yet any real-world damage has been done by it. The malware’s sophistication and infection of thousands of machines in Iran has led some to speculate that the U.S. or Israeli government built the code to take out Iran’s nuclear program.

Read more here
Some Android apps caught covertly sending GPS data to advertisers
From Ars Technica,
Read More here.
The results of a study conducted by researchers from Duke University, Penn State University, and Intel Labs have revealed that a significant number of popular Android applications transmit private user data to advertising networks without explicitly asking or informing the user. The researchers developed a piece of software called TaintDroid that uses dynamic taint analysis to detect and report when applications are sending potentially sensitive information to remote servers.
They used TaintDroid to test 30 popular free Android applications selected at random from the Android market and found that half were sending private information to advertising servers, including the user's location and phone number. In some cases, they found that applications were relaying GPS coordinates to remote advertising network servers as frequently as every 30 seconds, even when not displaying advertisements. These findings raise concern about the extent to which mobile platforms can insulate users from unwanted invasions of privacy.
Read More here.
Subscribe to:
Posts (Atom)